Discover has a neat account security feature: the ability to generate numbers that only work with one merchant. Imagine how handy this would be in the case of a credit card number breach! Only PayPal, arguably the biggest third-party payment processor in the solar system, won’t accept one of these numbers. It could have something to do with that third-party nature…or do they hate account security? That’s what Doug thinks. [More]
security

Apple And Amazon Quietly Change Security Procedures After 'Epic Hack'
It was inevitable that one of the companies called out in Mat Honan’s piece about a few hackers destroying his digital life would change some of the loophole-laden security procedures that helped the baddies gain access to the tech journalist’s accounts. So we’re relieved to learn that Apple and Amazon have both closed the particular weak spots that allowed a few determined people to reset all of Honan’s key passwords for services like Google and iCloud, and to remotely wipe the hard drives of all of his Apple devices connected to iCloud. [More]

TSA Flags Man With World’s Largest Penis For Additional Crotch Screening
Jonah Falcon of New York City is an actor and hosts a public-access show about the Yankees, but he isn’t famous for that. He’s famous for a quirk of nature: he has the largest recorded penis in the world. He’s appeared on lots of talk shows and even in a documentary, but evidently his fame hasn’t reached the TSA workers at San Francisco International Airport. There, the large bulge in his pants caught the notice of a guard, who presumed it was some kind of weapon. He was subjected to a (brisk and professional) extra patdown and tested for explosive residue. [More]

How To Create A Strong Password And Remember It
Following the hack of Zappos.com and 6pm.com there are probably quite a few of you looking for a way to create strong passwords and also remember them. Back in December, our safety-conscious friends at Consumer Reports ran a guide to creating strong passwords that are also easy… well, easier, to remember. Here it is. [More]

Places At Home To Stash Your Cash
Most financial experts don’t recommend keeping large amounts of cash stashed at home, but that doesn’t stop people from socking their savings in corners they believe to be safe. Those who do so leave themselves vulnerable to losing huge amounts of money due to burglaries or forgetfulness. [More]

Google Steps Up Browser Security To Keep Data Safe From Hackers
Internet common sense tells you to look for an “https” prefix on site URLs before offering up private information such as credit card numbers. Thanks to efforts from Google, sites with that security designation should be even more secure. [More]

Detect Hardware Trojans With "Singing Rings"
Researchers have proposed a new method for detecting trojan viruses embedded into hardware chips by using voltage detectors that “sing out” in a different frequency when they’re used on a tampered circuit. [More]

Senator Is Victim Of Credit Card Fraud, Thieves Rack Up $12,000 At Walmart
It’s a measure of the brazenness and ubiquity of identity theft that a U.S. Senator has become the latest victim of credit card fraud. Thieves stole the credit card numbers belonging to Senator Daniel Inouye (D) of Hawaii, embedded them on the magnetic strip of a fake credit card, and went on a $12,000 Walmart shopping spree. [More]

93,000 PSN Accounts Suspended After Latest Attack
PlayStation announced they’ve suspended 93,000 PSN accounts after the latest attack against their network. [More]

Freeze Your Credit Report
One way to protect yourself from identity theft is to “freeze” your credit report. This means that no new lines of credit can be opened in your name because lenders are prevented from taking a look at your credit report. This stops identity thieves from opening credit cards under your name and going on spending sprees. It also means extra hassle for you when you want to legitimately open credit. There’s always a tradeoff between security and convenience. Here’s how to do it. [More]
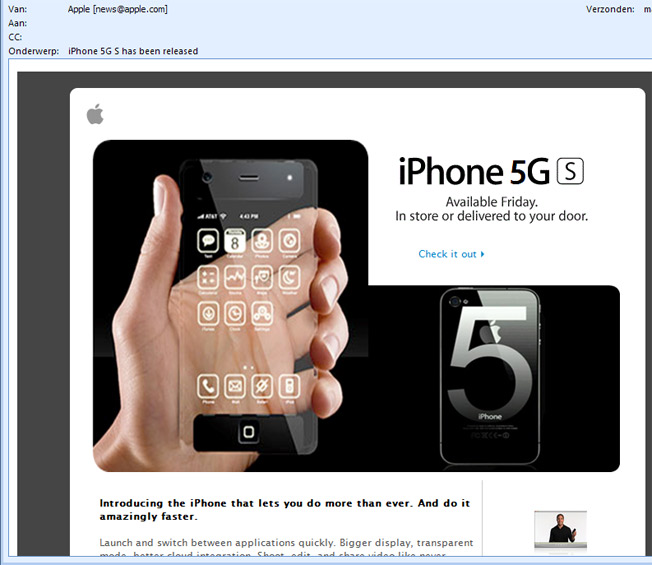
Fake iPhone 5 Emails Bear Malware
On the cusp of a big Apple event today where a new iPhone is expected to be announced, fake emails are going around purporting to give details of “the new Apple iPhone5GS,” featuring a see-through keyboard. Clicking on the links leads to a malware-laced website that targets PCs. Here’s the email and what to look out for. [More]

Secret Memo Reveals Which Cellphone Carriers Store Your Data The Longest
How long does your cellphone company keep logs of your text messages? Of the words you wrote? Of the calls you made? A Freedom of Information Act request by the American Civil Liberties Union of North Carolina unearthed a Department of Justice document that breaks down the retention periods for each mobile provider. [More]

Another Customer Sues Starbucks Over Bathroom Cam
After his 5-year-old daughter spotted a hidden camera in a D.C. Starbucks bathroom, a man is suing the company and asking for $1 million in damages on four counts, including breach of privacy. [More]

TSA Fires 28 Agents Who Allegedly Did Not Do Jobs
In the slow but inevitable reaction to the scandal in which several Transportation Security Administration agents were accused of letting un-screened baggage make it on to flights, the agency fired 28 employees. Fifteen others connected to the alleged negligence — which is believed to have occurred over several months in Hawaii last year — were suspended. Three others left their jobs voluntarily. [More]

This Craft Store Really Doesn't Trust Its Customers
When A. saw that a local craft store had a “no bags” policy, she assumed that meant that the store didn’t allow shopping bags from other stores. No, it refers to purses and other personal bags. It’s not a huge hardship to lock one’s purse up and carry one’s wallet around in order to browse a store, but it is awfully annoying. [More]

Web Analytics Firm, 20 Clients Sued For Web Tracking
There’s big business in tracking web browsing, and temptation to grab more information than is legally acceptable. A lawsuit alleges a web analytics company and its clients stepped over the line in snooping on browsing habits, particularly of those who try to cover their tracks. [More]

Mocking Hacker Stock Photo Art
It can be so hard to find just the right photo to illustrate a story about hacking. Luckily, stock photo agencies have stepped up to the challenge. [More]



