Secure Messaging Scorecard Shows Just How Unprotected Your Online Chats Are
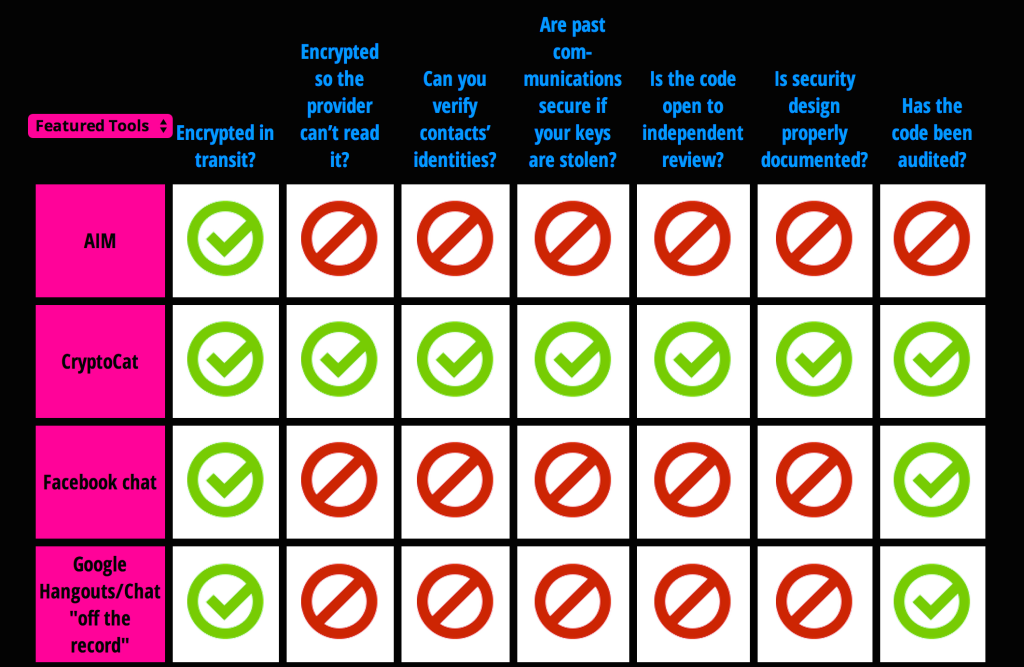
Results for four of the 39 services currently evaluated on the EFF’s Secure Messaging Scorecard.
Thankfully, the folks at the Electronic Frontier Foundation had some time on their hands and put together a handy scorecard so you can not only look at what a particular service does or doesn’t do to protect its users, but also compare the various messaging services.
The EFF looked at seven different categories (see below for more details) to evaluate each service, ranging from the whether or not your messages are encrypted from end-to-end to the transparency and documentation of the cryptography used to a requirement for timely independent auditing.
Of the 39 services on the scorecard — which includes popular offerings like AIM, Facebook chat, FaceTime, Google Hangouts, iMessage, Skype, Snapchat, and Whatsapp — only six (ChatSecure, CryptoCat, Signal/Redphone, Silent Phone, Silent Text, and TextSecure) received green checkmarks in all categories.
Users of Apple’s iMessage and FaceTime may be glad to know that they were the most secure of the big-name services on the scorecard, qualifying for good marks in 5 of 7 categories.
But many of the most popular names failed at all but the most basic level of security. Services like AIM, Google Hangouts, Facebook Chat, Yahoo, WhatsApp and even Apple’s e-mail products, fail to provide end-to-end encryption of messages, meaning the service provider can have unencrypted access to the content of your messages.
Some of the bigger names, like AIM and Yahoo, only received one green check on the scorecard because their services haven’t even been independently audited in the previous 12 months.
Popular Chinese messaging service QQ and Mxit from South Africa were the true flunkies on this scorecard, failing to encrypt messages at any point.
“Many new tools claim to protect you, but don’t include critical features like end-to-end encryption or secure deletion,” explains EFF Technology Projects Director Peter Eckersley. “This scorecard gives you the facts you need to choose the right technology to send your message.”
Below are more details on the seven categories used for the scorecard. The EFF provides additional information in its Methodology section of the card.
1. Are messages encrypted in transit? That is, if someone were able to tap into your connection, would they need to decrypt the message before being able to read it?
2. Are messages encrypted so that the service provider can’t read it? This offers even more privacy, as not even the people at the company powering the message exchange can see what you’re sending.
3. Can you verify contact’s identities? This is more technical in nature, but involves giving users some sort of method for verifying that the person they are speaking with is the intended correspondent. It doesn’t mean that you can verify that SallyJonesXZ&Z1 is in real life your Uncle Jim, but that someone can’t impersonate SallyJonesXZ&Z1 on the service.
4. Are past communications secure if your keys are stolen? Another technical-sounding one. This is a check to see that “if users choose to delete their local copies of correspondence, they are permanently deleted.”
5. Is the code open to independent review? This looks at whether a service can make available relevant parts of its code to check for “bugs, back doors, and structural problems.”
6. Is the crypto design well-documented? Here the EFF asks if the developer can provide “clear and detailed explanations of the cryptography used by the application,” preferably in a white-paper written for review by an audience of professional cryptographers.
7. Has there been an independent security audit? This requires that an independent, qualified security team has audited the service in the previous 12 months. In most cases, this audit would come from an outside organization, but EFF allows for larger companies with internal-but-independent auditing teams to qualify.
Want more consumer news? Visit our parent organization, Consumer Reports, for the latest on scams, recalls, and other consumer issues.

