Never Click On "Free Public Wifi"
(zcopley)
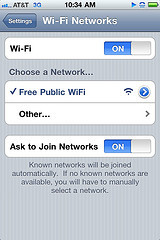
When you’re cruising for a hotspot at a coffee shop, never click on the “Free Public Wifi” wireless network. “Free Public Wifi” is a Windows XP quirk; when a computer can’t find any of its favorite networks it creates a network on-the-fly, but it doesn’t go anywhere. At best, you’ll never connect to the internet. At worst, you could be exposing your computer to hackers.
Windows XP users should make sure they’re upgraded to Service Pack 3, which fixes it so your computer doesn’t broadcast the “Free Public Wifi” network.
The Zombie Network: Beware ‘Free Public WiFi’ [NPR via Lifehacker via Galleycat]
Want more consumer news? Visit our parent organization, Consumer Reports, for the latest on scams, recalls, and other consumer issues.

