Lenovo Gets Slap On Wrist From Feds Over Pre-Installed Ad Software With Gaping Security Hole
Remember that time that Lenovo sold all those laptops with crappy ad-injection software built in, leaving users at risk for both bottom-of-the-barrel advertising and cyber attacks? Today, the tech company settled a complaint with the Federal Trade Commission, promising not to do this all again and not paying a penalty for its alleged transgressions.
Starting in the summer of 2014, Lenovo began selling laptops that included software called VisualDiscovery from a company called Superfish. For those not familiar with ad-injectors, they’re a way for a third-party to make your web-browsing experience even more obnoxious and ad-filled by inserting additional advertisements via pop-up ads and other things that no one with a soul actually appreciates.
According to the FTC complaint [PDF] against Lenovo, the company not only made a deal with Superfish to install this unwanted crud on new laptops, Lenovo also demanded that the ad-injector work on every web browser on the computer — including any browser installed after purchase.
VisualDiscovery also managed to inject ads on connections that are supposedly secure via https. See, when you’re communicating with a secure site, that site transmits a security certificate to your browser — basically a secret handshake that indicates to your computer that you’re actually on the website for Big Bob’s Bank and not some scammer who set up a clone of the Big Bob’s Bank website.
What VisualDiscovery did was insert itself into this conversation, accepting the secure site’s certificate then passing on its own certificate to your browser. This means that VisualDiscovery was acting as the man-in-the-middle, decrypting and and re-encrypting all the data you thought you were sending to and receiving from the secure website.
If that weren’t problem enough, Superfish stupidly — like, world class stupid — used the same security certificate every time to interrupt secure traffic… for every user, of every affected Lenovo.
A cybercriminal would have needed only to create a fake secure site using Superfish’s credentials to siphon off personal data from every user that visited it. Affected Lenovo users had no way of knowing that the sites they visited were authentic or not.
Within weeks of Lenovo unleashing this idiocy on the world, users began to complain and raise concerns about the security problems with VisualDiscovery. Lenovo responded by eventually updating the VisualDiscovery software on new laptops, but did not push out an update for those unlucky folks who had purchased a Lenovo with the gaping security flaw.
What really landed Lenovo in tepid water with the FTC was the company’s failure to disclose to customers that their new computers came with VisualDiscovery, and that the software was effectively hidden from users who didn’t navigate into the various folders in their PC’s Control Panel.
The only disclosure of VisualDiscovery came in a one-time pop-up window for each user. The first time a Lenovo owner opened a browser window on their new computer, the pop-up stated, “Explore shopping with VisualDiscovery: Your browser is enabled with VisualDiscovery which lets you discover visually similar products and best prices while you shop.”
There was an opt-out link in the pop-up box, but the complaint contends that it was too small. Additionally, there is no indication that the user is agreeing to or accepting this software; clicking anything but the opt-out was considered to be an acceptance of VisualDiscovery’s continued use.
The following screengrab from the FTC complaint gives you some idea of what that pop-up and opt-out looked like:
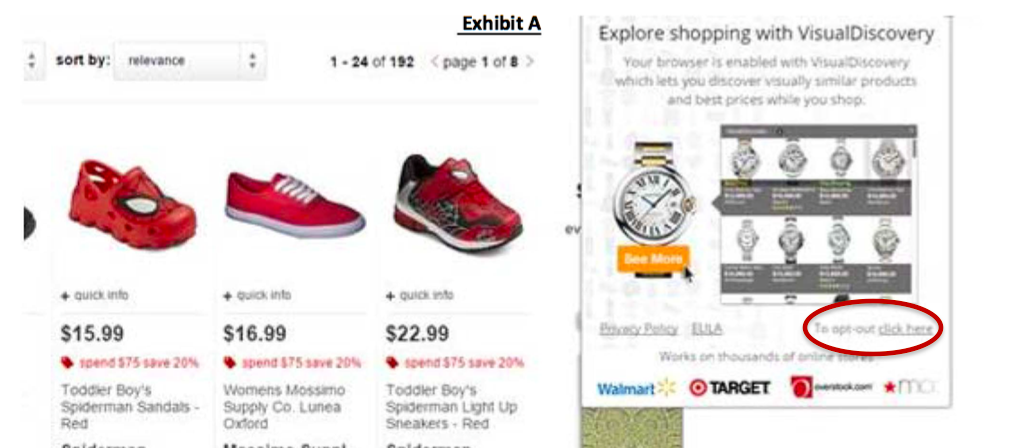
And even if there were some sort of “I Agree” button on the pop-up, the FTC notes that the notice fails to disclose the fact that VisualDiscovery would be interrupting and decrypting your connections to secure websites. This inane and insane aspect of the software was not even disclosed in the fine print of the privacy policy, says the FTC.
Also, the opt-out didn’t stop VisualDiscovery from acting as the man-in-the-middle. It just stopped the software from using that access to inject ads into your browser.
As part of the settlement [PDF] announced today, Lenovo is “prohibited from misrepresenting any features of software preloaded on laptops that will inject advertising into consumers’ Internet browsing sessions or transmit sensitive consumer information to third parties.” In other words, it must obey the law.
Lenovo must also get customers’ affirmative consent before pre-installing this type of software and implement — for the next 20 years — a comprehensive software security program for most of the consumer software that comes preloaded on its laptops. In all, some 750,000 laptops were sold containing this horrid software.
But one thing Lenovo won’t have to do is pay the FTC or any Lenovo customers a single dollar. Acting FTC Chair Maureen Ohlhausen explained at a Tuesday morning press event that the FTC doesn’t have the authority to obtain civil penalties for first-time violations of the FTC Act. The commission can seek civil penalties in cases involving other specific laws over which it has enforcement authority — like the Children’s Online Privacy Protection Act — or for violations of the various industry-specific rules created by the FTC.
But the FTC Act — and its generalized prohibitions against unfair or deceptive business practices — does not allow for the commission to seek a financial penalty for initial violations. Failure to comply with an FTC Act-related settlement could, however, result in financial penalties for a company.
Ohlhausen also pointed out that Lenovo would experience some financial sting from the settlement due to the internal costs of the 20-year software security program it must implement.
Deceptive or not?
While the two sitting FTC commissioners (there are still three vacancies, including the chairmanship) agreed that the failure to adequately disclose the numerous troubling aspects of VisualDiscovery amounted to an unfair business practice, they disagreed on whether or not it rose to the level of a deceptive business practice.
Commissioner Terrell McSweeny argued in a statement [PDF] that Lenovo may have actively deceived customers by intentionally hiding software that had such a negative impact on the browsing experience. In addition to the privacy and security problems, and the unwanted ads, VisualDiscovery also slowed download speeds by around 25% and upload speeds by 125%.
“I believe that if consumers were fully aware of what VisualDiscovery was, how it compromised their system, and how they could have opted out, most would have decided to keep VisualDiscovery inactive,” writes McSweeny, saying that this allegation should have been included in the complaint. “The FTC should not turn a blind eye to deceptive disclosures and opt-ins, particularly when consumers’ privacy and security are at stake.”
However, Acting Chair Ohlhausen, disagreed, saying in her statement [PDF] that “Lenovo did disclose that the software would introduce advertising into consumers’ web browsing, although its disclosure could have been better.”
Ohlhausen also contends that — to the extent that consumers have any expectations of ad-injection software — “they likely expect it to affect their web browsing and to be intrusive.”
The ads injected by VisualDiscovery “may have been irritating to many,” writes Ohlhausen, but the did not render the software unfit for its intended use. “Therefore, I do not find Lenovo’s silence about those features to be a deceptive omission.”
In a statement released this morning, Lenovo says it stopped pre-installing VisualDiscovery in early 2015 and that it knows of no instances of the false security certificates being exploited by a third party.
Want more consumer news? Visit our parent organization, Consumer Reports, for the latest on scams, recalls, and other consumer issues.

