Researcher Says It Only Takes Minutes To Hack Most Smart Home Security Devices
(erocsid)
Gigaom reports that testing conducted by research firm Synack found that many of the products that makeup a smart home – including cameras, thermostats, and smoke detectors – have serious security flaws.
Colby Moore, a security research analyst for Synack, tells Gigaom that it took him only 20 minutes to break into all but one of the 16 assorted devices during testing.
Moore says the lack of security for such products could stem from the fact that there are no set standards for smart home security.
“Right now the internet of things is like computer security was in the nineties, when everything was new and no one had any security standards or any way to monitor their devices for security,” he tells Gigaom.
Of the 16 devices tested, Synack found only one – the Kidde connected smoke detector – that didn’t have significant flaws.
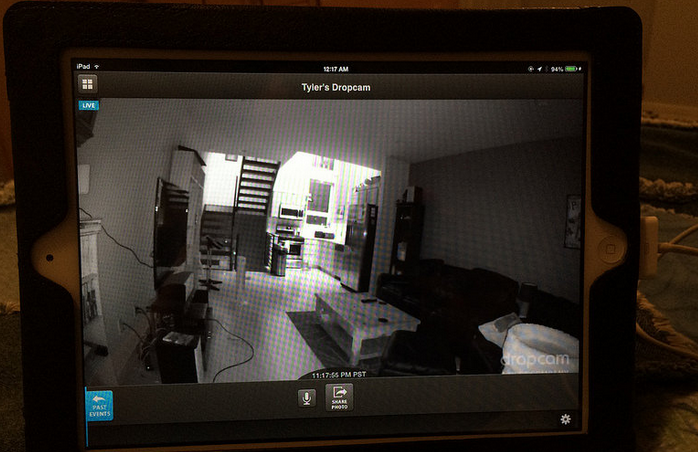
When all testing was said and done, the worst performing devices were connected cameras. Each of the five camera products tested had issues either with encryption or password security. In all, the report found that Dropcam was the least-flawed camera.
When it came to thermostats, Nest was deemed to be the most secure, although it did lose points for a weak password policy. Other products from Ecobee, Hive and Lyric were both dinged by testers for issues with password policies, encryption and a long history of vulnerabilities across product lines.
While researchers already found the Kidde connected smoke detector to be the most secure out of all smart home devices tested, other smoke and carbon dioxide detectors didn’t fare so well.
Moore points out that this category – specifically the First Alert product – could fall victim to a supply chain-based attack. Gigaom suggests that means someone would have to intercept the device and change a component, something that could take place in returned or second-hand devices.
The final category tested by Synack was home automation controllers – the devices that connect all smart home devices.
Iris tested the best, only being dinged for its moderate password policy. Other products from SmartThings and Control4 had issues with exposed service and insecure architecture.
In all, Moore tells Gigaom that the security of smart home devices today is “abysmal.”
Still, he does offer consumers a few best practices that they could follow to make their devices safer.
He suggests users hardwire as many devices as possible, enable automatic firmware updates and utilize strong passwords.
When it comes to smart home security, cameras are the worst [Gigaom]
Want more consumer news? Visit our parent organization, Consumer Reports, for the latest on scams, recalls, and other consumer issues.

