After a rash of account breaches on social media networks like MySpace, LinkedIn, Tumblr, and Twitter, the latest site to fall victim to hackers seems to be Yahoo, with a hacker claiming he’s got account information for 200 million users and is selling those credentials on the internet’s black market. [More]
hackers

Man Accused Of Hacking United Airlines Website, Stealing Travel Vouchers
There are a few ways you can earn travel vouchers that let you fly on the cheap or for free, but slipping in the back door and stealing them could also earn you a trip to court. That’s the lesson playing out right now in Utah, where officials charged a man with a slew of crimes including theft after he allegedly hacked United Airlines and boosted unredeemed vouchers. [More]
Government Asking People To “Hack The Pentagon” To Find Security Flaws
The Pentagon is joining a long list of companies and organizations in opening the door to hackers by asking for the public’s help in testing the cybersecurity infrastructure of some of its websites. [More]

Widespread Flaw Could Allow Hackers To Hijack Your Wireless Mouse Or Keyboard
It can surely be convenient to plug a dongle into your computer’s USB port and use a mouse or keyboard without the hassle of wires everywhere, but according to a new report from an Internet of Things security company, many wireless keyboards and mice are vulnerable to hackers. And once an attacker has access to those peripherals, they could easily download malware or steal information from your devices. [More]

Hyatt Confirms 250 Hotels Were Infected With Malware Last Year, Possibly Exposing Customer Payment Data
After announcing late last year that a slew of its hotels had been infected by malware, Hyatt has now identified the 250 properties that were affected — roughly 40% of its businesses in operation. Customers staying at those hotels who paid with a debit or credit card may have had their payment data and other information exposed to hackers, the chain said. [More]

Toy Maker VTech Hires Cyber Forensic Team To Help Beef Up Security After Data Breach
After a data breach at popular kids’ toy maker VTech that put the personal information of nearly five million parents and children at risk, as well as reportedly exposing many of their photos and chat logs, the Hong Kong-based company says it’s bringing in the pros to help shore up its security. [More]

Former Ashley Madison Customer Sues Site Over “Army Of Fembots” With Fake Profiles
After hackers dumped a plethora of personal information about Ashley Madison’s 37 million subscribers online in August, the public has learned a lot about the dating site aimed at cheaters. Among the reported revelations: only about 15% of its users are women, contrary to the site’s marketing claims, a new lawsuit says. Adding insult to injury? The army of fembots scattered through the sites with fake profiles written by employees. [More]

Security Researcher Successfully Steals Home WiFi Passwords By Hacking Into Tea Kettles
While it might be super convenient to have everything in your home connected to the Internet, that interconnectivity can also give attackers a chance to sneak in through seemingly innocent devices. Take the humble tea kettle: a security researcher in England has been hacking into smart kettles across the country and gaining access to private WiFi networks. [More]
Crowdfunding Site Patreon Hacked, 15GB Of Donor Info Dumped Online
Patreon, a website that allows donors to give regularly to sites, artists, projects and other creators, yesterday evening that it’d been hit by a hack attack that accessed some registered names, email addresses and mailing addresses. And according to reports, 15GB of data was then dumped online, exposing information about donors and the projects they’ve funded. [More]

Hilton Looking Into Possible Hack Attack Affecting Guests Using Credit Cards At Its Restaurants, Gift Shops
Hilton Hotels says it’s looking into a possible hack attack connected to point-of-sale registers and a variety of Hilton properties. If you bought something at a restaurant, gift shop or other store at a Hilton property recently, you should take a closer look at your credit card statements for any fraudulent activity. [More]

Apple Pulls Malware-Infected Apps After App Store Suffers Its First Major Breach
Hackers have finally taken a bite out of Apple’s App Store: the company confirmed that attackers were able to infect some of the apps it offers with malware, by copying and modifying a tool used by software developers. Apple says it has now removed the affected apps from the App Store. [More]

Uber Hires Security Researchers Who Hacked A Jeep To Protect Its Self-Driving Cars From Cyber Attacks
As technology advances and our cars become more and more autonomous, they are also opened up more and more to a new danger that didn’t used to exist on the roads — hack attacks. To protect that new technology and reassure future customers that riding in self-driving cars can be safe, Uber has hired the same two vehicle security researchers who managed to remotely hack a Jeep earlier this summer. [More]

Ashley Madison CEO Steps Down In Wake Of Hacking Scandal
Less than two weeks after hackers published two big data dumps full of material stolen from Ashley Madison, a dating website for cheaters, its parent company Avid Life Media announced that effective today, CEO Noel Biderman will be stepping down from his position and is no longer with the company. [More]

IRS: Identity Thieves Accessed More Taxpayer Accounts Than We Thought
Almost three months after the Internal Revenue Service said identity thieves accessed more than 100,000 taxpayer accounts in its databases, the agency says that a review shows more accounts were exposed and there were more attempts to gain access to them than previously reported. [More]

Report: Hackers May Have Breached Sabre Reservations Systems, American Airlines
Another day, another report that says hackers have been busy plundering major companies. Insiders say the same group of hackers believed to be behind security breaches at Anthem Inc. and the U.S. government’s personnel office have two more victims: Sabre Corp., which processes reservations for hundreds of airlines and thousands of hotels, and American Airlines. [More]

Jeep Cherokee Owners File Lawsuit Against Fiat Chrysler, Harman After Hackers Wirelessly Hijack Vehicle
It was inevitable: A few weeks after hackers showed that a Jeep Cherokee could be hijacked remotely, three car owners have filed a lawsuit seeking class-action status against Fiat Chrylser Automobiles and Harman International, the maker of the Uconnect onboard infotainment system. [More]

Yahoo Removes Malware From Its Advertising Network That Exploited Weakness In Adobe Flash
For six days last week, malware known as “malvertising” was reportedly lurking in Yahoo’s advertising network, with the potential for attackers to infect internet users’ computers and hold them for ransom. Security researchers say they notified Yahoo of the malware upon discovering it on Sunday, and the company removed the malicious code immediately. [More]
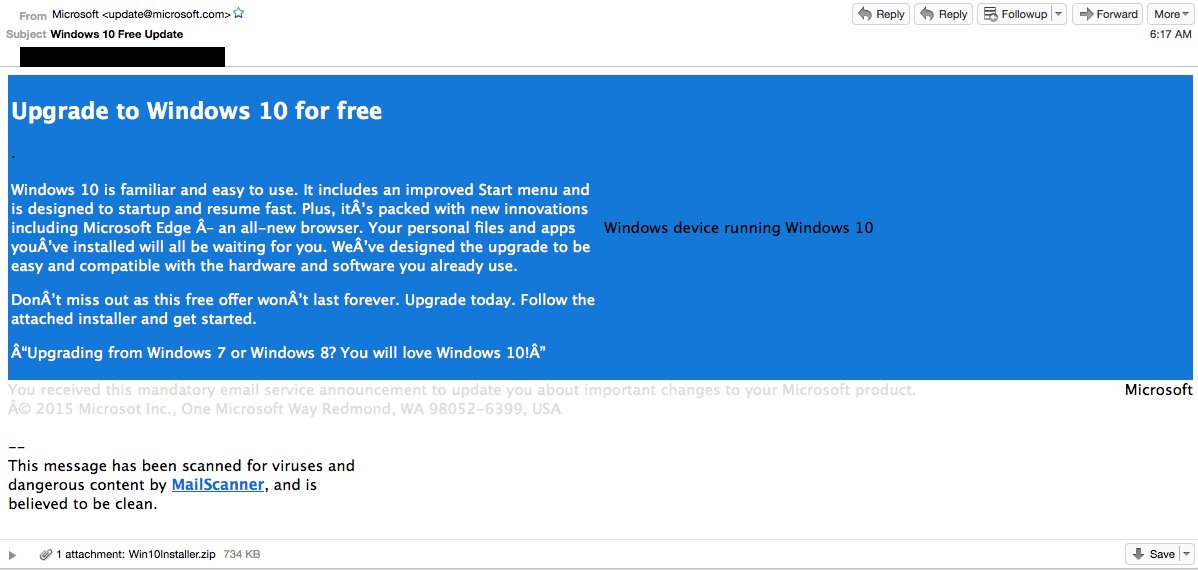
Scam Alert: Microsoft Is Not Upgrading Computers To Windows 10 Through Email
First and foremost: If you’re a Windows 7 or 8 user, Microsoft will not email you to upgrade to Windows 10. If you do get an email along those lines, it’s probably a scam and if you download what’s inside, bad guys could hold your computer’s files for ransom. [More]