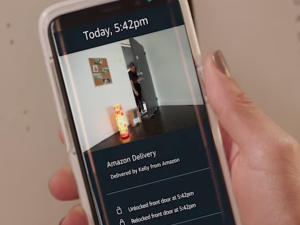
As it was predicted, so it has come to pass: In an effort to combat “porch pirates” who love swiping any boxes left outside, Amazon is launching a new service that allows delivery people to walk into customers’ homes to drop off packages. [More]
Search results for: security key

The Many Ways In Which Your Kid’s Smartwatch Can Be Hacked
Most of us aren’t going to spend hundreds of dollars on an Apple Watch for our kids, but there are many less-expensive, kid-targeted smartwatches available. Unfortunately, a new report claims that your young one’s tiny screen may also be a huge privacy risk. [More]

Exploding Sunroofs: Danger Overhead
When it happened, Heather Savage had two of her five children with her in their 2016 Nissan Pathfinder. Four-year-old Eli was strapped into a car seat in the second row, and Raquel, 15, whom they’d just picked up from ballet class, was in the front passenger seat. [More]

Can The President Actually Take Away A Network’s Broadcast License For “Fake News”?
Irked by an NBC News story he claims is false, President Trump stated this morning that it may be time to “challenge” the network’s broadcast license. But what does that even mean — and would the Trump administration have the authority to yank a TV station’s access to the airwaves over a news story? [More]

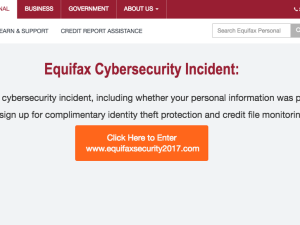
Equifax CEO Apologizes For Company’s Incompetence, Promises Vague (Possibly Pointless) Credit ‘Lock’ Service In 2018
The interim CEO for credit bureau Equifax is finally issuing a full-throated mea culpa for the massive data breach that compromised sensitive personal and financial information for about half of the adult U.S. population. In addition to extending the deadline for hack victims to freeze their credit free of charge or sign up for the company’s not terribly enticing anti-ID theft program, Equifax is also promising to offer something new: A way to “lock” your credit file (sort of, maybe, and only partially) for free (possibly). [More]

Senate Plans Meaningless Hearing On Obamacare Repeal Bill
One of the reasons that the effort to repeal the Affordable Care Act met a dramatic late-night demise in July was the criticism that GOP lawmakers held no actual hearings on this matter that could directly impact many millions of Americans. As Republican senators look to make one last try at repeal before their clock runs out, legislators are finally holding their first, but ultimately pointless, public hearing on healthcare. [More]
Two Equifax Execs Exit Company Following Massive Data Breach
The full extent of Equifax’s recently revealed, massive data breach isn’t known yet — although 143 million US customers and tens of millions of others globally are thought to be affected — but top executives are already having to answer for the debacle, with two Equifax officers making a sudden exit. [More]

Hacker Broke Into Hotel Rooms Electronically, Stole Customers’ Stuff
Key cards may be a convenient way for hotels to issue room keys, but a bug in one popular model made it convenient to electronically pick the locks. An override code to open doors was programmed into the locks, making them easy to open after a quick shopping trip to RadioShack. One man took advantage of this bug and used it to gain access to rooms across the country, stealing stuff from hotels and guests alike. [More]

Uber Settles Federal Allegations It Deceived Customers About Privacy & Data Security
Uber has reached a deal with the Federal Trade Commission to settle the government’s investigation into the ride-hailing service’s allegedly questionable privacy practices.
[More]

FBI To Parents: Watch Out For Kids’ Privacy With Internet-Connected Toys
A basketball, a Lego set, or a box of crayons is largely what it seems, but modern “smart toys and entertainment devices” for kids have a lot of things in them that can collect sensitive data. And as more and more of a kid’s nursery fills up with gadgets that connect to Bluetooth, the web, or parent apps, the feds are advising parents to be wary. [More]

Teen Falls From Six Flags Ride, Other Park Guests Catch Her
Several guests at a Six Flags amusement park in New York worked together over the weekend to catch a teen dangling from a ride, video from the tense situation shows. [More]

6 Key Allegations From The D.C. & Maryland Lawsuit Against President Trump
This morning, the attorneys general for both the state of Maryland and the District of Columbia filed a federal lawsuit against President Donald Trump, accusing him of violating the so-called “emoluments clauses” of the U.S. Constitution by continuing to own his various business hotel, restaurant, golf, and real estate ventures. But what are the exact allegations being brought in this case? [More]

Your Car Could Be The Next Ransomware Target
The recent “WannaCry” ransomware attack that crippled computer systems around the globe has highlighted the digital vulnerabilities in our daily lives. [More]

Motorcycle Gang Members Used Key Codes To Boost $4.5M Worth Of Jeep Wranglers
All it took was a few stolen key designs and computer codes for a biker gang to successfully steal more than 150 Jeep Wranglers — valued at $4.5 million — from the U.S. and relocate them to Mexico in a years-long heist. [More]

Do You Use OneLogin? Change Your Password Now
If you use OneLogin to keep all your, well, login information straight, it’s time to change your password, as the password manager’s U.S. data centers are at the center of the latest hack attack. [More]